Is the National Security Agency collecting and storing data on fewer telephone calls than we thought? So say reports in the Wall Street Journal, Washington Post, andNew York Times."Although intelligence officials have indicated since last summer that the National Security Agency was vacuuming up nearly every American telephone record for counter-terrorism investigations," the L.A. Times reports says the LA Times in its version, "officials acknowledged Friday that the spy agency collects data from less than a third of U.S. calls because it can't keep pace with cellphone usage."
That's a momentous development.
If true, virtually every news article and analysis piece you've read about the phone dragnet overstated how comprehensive it is. The L.A. LA Times story continues:
Rather than sweeping in all U.S. call records, officials said, the NSA is gathering toll records from most domestic land line calls, but is incapable of collecting those from most cellphone or Internet calls ...
calls...The officials, who spoke on condition of anonymity because much of the program remains classified*, said they did not correct the public record because they did not want to tip off potential adversaries to obvious gaps in the coverage. "We didn't want to tell the bad guys to go out and get a cellphone," one senior intelligence official said.
What perplexes me is why anyone in the executive branch would want this out there. It there: it can't help but reflect poorly on the national-security national security state. If these stories are false, you understand, current and former U.S. officials are lying. And if the stories are true, even in a narrow, accurate-but-misleading sense? If the NSA really collects just a third of phone metadata and almost no cellphone cell metadata under Section 215? That would prove that important NSA overseers have little idea what's going on. It would prove that more effort needs to be put into oversight.
Think about it:
1) Numerous members of Congress, including legislators with a particular interest in surveillance issues (e.g., Justin Amash, James (e.g. Amash, Sensenbrenner, etc.) have operated for months now under the belief that data on virtually all calls is tracked under Section 215. As James Sensenbrenner put it in a letter to Eric Holder, "the administration has collected the details of every call made by every American, even though the overwhelming majority of these calls have nothing to do with terrorism." Is this widespread belief among legislators wrong, and if so, isn't that alarming?
What else don't they understand?
2) Two federal judges have ruled on the constitutionality Constitutionality of the Section 215 program, reaching opposite conclusions. But if you read their opinions, both of them believed that metadata was being gathered on virtually every telephone call in the United States, States., and that belief played a non-trivial role in their published opinions.
Here's Judge William H. Pauley, who ruled in the Obama Administration's favor (emphasis added):
This blunt tool only works because it collects everything. Such a program, if unchecked, imperils the civil liberties of every citizen. Each time someone in the United States makes or receives a telephone call, the telecommunications provider makes a record of when, and to what telephone number the call was placed, and how long it lasted. The NSA collects that telephony metadata. If plumbed, such data can reveal a rich profile of every individual as well as a comprehensive record of people's associations with one another.
In response to the unauthorized disclosure of the Secondary Order, the Government acknowledged that since May 2006, it has collected this information for substantially every telephone call in the United States, including calls between the United States and a foreign country and calls entirely within the United States.
Later in the opinion he says this:
The ACLU argues that the category at issue-all telephony metadata-is too broad and contains too much irrelevant infonnation. That argument has no traction here. Because without all the data points, the Government cannot be certain it connected the pertinent ones. As FISC Judge Eagan noted, the collection ofvirtually all telephony metadata is "necessary" to permit the NSA, not the FBI, to do the algorithmic data analysis that allow the NSA to determine "connections between known and unknown international terrorist operatives.
If the government now acknowledges that it has less than a third of the data points anyway, one of the judge's specific arguments against the ACLU falls apart.
And here's Judge Richard Leon, who ruled that the Section 215 metadata program is unconstitutional:
Straining mightily to find a reason that plaintiffs nonetheless lack standing to challenge the metadata collection, the Government argues that Judge Vinson's order names only Verizon Business Network Services as the recipient of the order, whereas plaintiffs claim to be Verizon Wireless subscribers. The Government obviously wants me to infer that the NSA may not have collected records from Verizon Wireless (or perhaps any other non-VBNS entity, such as AT&T and Sprint). Curiously, the Government makes this argument at the same time it is describing in its pleadings a bulk metadata collection program that can function only because it "creates an historical repository that permits retrospective analysis of terrorist-related communications across multiple telecommunications networks, and that can be immediately accessed as new terrorist-associated telephone identifiers come to light."
Put simply the government wants it both ways. Virtually all of the government's briefs and arguments to this Court explain how the Government has acted in good faith to create a comprehensive metadata database that serves as a potentially valuable tool in combatting terrorism–in which case, the NSA must have collected metadata from Verizon Wireless, the single largest wireless carrier in the United States, as well as AT&T and Sprint, the second and third-largest carriers. Yet in one footnote, the Government asks me to find that plaintiffs lack standing based on the theoretical possibility that the NSA has collected a universe of metadata so incomplete that the program could not possibly serve its putative function. Candor of this type defies common sense and does not exactly inspire confidence!
In a footnote, Judge Leon tries to capture how important the premise of a cell-phone inclusive, comprehensive dragnet is to the state's argument. "To draw an analogy," he writes, "if the NSA's program operates the way the Government suggests it does, then omitting Verizon Wireless, AT&T, and Sprint from the collection would be like omitting John, Paul, and George from a historical analysis of the Beatles. A Ringo-only database doesn't make any sense, and I cannot believe the Government would create, maintain, and so ardently defend such a system."
Wouldn't it be alarming if both of the federal judges who've ruled on these cases didn't have a core piece of factual information directly relevant to their opinions?
3) The Privacy and Civil Liberties Oversight Board, an independent executive branch agency, also reviewed the Section 215 program with access to classified data. Its Chairman, David Medine, gave written testimony to the House Judiciary Committee:
Detailed rules limit the NSA’s use of the telephone records it collects, and the Board’s report describes them at length. But while those rules offer many valuable safeguards designed to curb the intrusiveness of the program, in the Board’s view they cannot fully ameliorate the implications for privacy, speech, and association that follow from the government’s ongoing collection of virtually all telephone records of every American.
See the problem? If the latest Section 215 stories are true, people in all three branches of government, many with direct oversight responsibility and access to classified documents, were still ignorant about how the most well known NSA program works—ignorant works – ignorant in part because national-security national security officials misled them about the program.
Did whoever approved that anonymous leak realize that it would reveal NSA oversight to be inadequate, and make two judges, an executive-branch 2 judges, an executive branch overseer, and numerous legislators seem ignorant despite the security clearances that they enjoy?
__
* Is_____
** For **For example:
- All seem to be referring to the bulk telephone metadata collection program allegedly authorized by Section 215 of the Patriot Act, though they're written in a way that makes it hard to tell. Could it be that the U.S. is collecting less metadata than was formerly thoughtunder that specific program, but is still collecting most U.S. cellphone
cell phonemetadata under a different authority, or else getting it from our surveillance partners at GCHQ? - Why is this seemingly sanctioned leak coming out now?
- If U.S officials didn't want to tip off adversaries to gaps in the coverage, what changed?
- Seriously, "We didn't want to tell the bad guys to go out and get a cellphone"? How many terrorists were plotting from the land line at their home?
- By all accounts, the NSA believes it has a legal right to collect all cellphone
cell phonemetadata, and it has the desire to do so as well. Is it really plausible that they've just been leaving it untouched, given everything else we know about them? As I'll go on to explain, it contradicts so much of what we've been told.













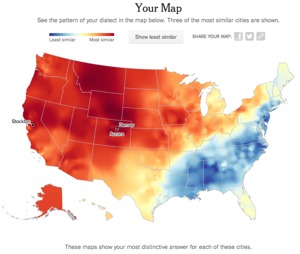 The New York Times has a 25-question, multiple choice survey about word usage and pronunciation (e.g., "How to you pronounce "aunt?").
The New York Times has a 25-question, multiple choice survey about word usage and pronunciation (e.g., "How to you pronounce "aunt?").  This animated gif of a chain-making machine is mesmerizing.
This animated gif of a chain-making machine is mesmerizing.